Article State & Local Government Data Centers: Managing Growing IT Demands, Costs and Risks
State and local government data centers are struggling to keep pace with the needs of the agencies and constituents they support, and that gap is increasing with the growing amount of data and security threats in today's world.
By Insight Editor / 20 Sep 2016 / Topics: Data center

These government agencies are uniquely challenged to fulfill their evolving mission for two reasons:
- They feel weighed down by legacy data center architectures and approaches.
- They are faced with budget pressures and/or staff limitations that hinder the ability to simultaneously maintain service levels and properly chart a path forward.
Key challenges
Agency data centers must be agile enough to address megatrends like the growth of data analytics, the digital transformation of longstanding processes, and the growing threat of cyberattacks and data breaches. But developing this agility often requires some difficult decisions: expanding, consolidating or relocating data centers, embracing new architectures and models, or transitioning operations from one organization to another.
In the face of such massive challenges and resource-intensive solutions, many state and local governments are unsure where to even begin. This daunting task often falls on overworked data center managers who are charged with identifying the most mission-effective and cost-effective path to align the evolving needs of their constituents to an ever-changing array of computing, storage, networking, monitoring and management options.
However, three overarching needs are consistent across almost every effort for data center management:
- The need to meet the expanding IT demands of the government agencies and constituents they support
- The need to effectively manage IT costs tactically when budgets contract and strategically when budgets expand
- The need to address new threats and security risks as network technology evolves
Managing IT costs
As shown in Figure 1, worldwide IT spending on data center systems are on the rise with forecasted spending for 2020 amounting to $185 billion. However, most data center leaders realize that the less they spend on ongoing maintenance, the more they can devote to building new systems and solutions for their agency and constituent needs.

So, instead of working on the new value-producing projects that would better serve their missions, many IT personnel spend the bulk of their time and budget maintaining existing systems. This reality can set up an adversarial relationship between IT and the agencies they serve, with mounting frustration on both sides. Government agencies and departments often feel that IT is unresponsive to their needs; on the other hand, IT feels stretched thin and struggles to keep up.
The challenges posed by the maintenance of legacy systems also has the undesirable effect of driving up IT-related expenses at a time when leaders are under nearly constant pressure to reduce IT spending. In order to find the savings they need, IT leaders often evaluate two different options:
- They may consider proprietary vendor systems that promise to reduce overall costs right away. Although these solutions may reduce total cost of ownership (TCO) in the short term, they limit long-term choice. Over time, organizations can find themselves locked in to one specific vendor, once again forcing them to confront problems caused by inflexible infrastructure.
- IT leaders may deploy commodity hardware and open-source software. The low acquisition costs for these solutions are attractive, but unless organizations have a large and experienced IT staff, maintaining these systems requires time and effort — potentially leading them right back where they started.
During the discovery process to bridge these opposing perspectives, many state and local data centers fear missing key insights due to ineffective discovery, or wasting time and resources trying to capture every detail of their IT infrastructure.
Again, the path forward requires more than just hardware consulting and migration project management — it requires a strategic understanding of mission-critical systems paired with an open, agnostic approach to appliance and network hardware that accommodates hybrid solutions to achieve mission goals.
Managing demands
For many state and local government data centers, there is a significant pain in the gap between current capabilities of data center operations and where they need to be. They often experience symptoms of legacy systems not holding up to newer and expanded agency requirements, or situations where maintenance budgets are so large that they cannot move forward with new projects and initiatives.
From a legacy perspective, many agencies are tied to outdated operating systems like Windows Server 2003 or Windows XP, paying onerous expenses to continue supporting such outmoded systems well after end of life. While upgrade paths are known and affordable to such agencies, there are often many home-grown applications version-locked to those operating systems that the mission impact of updating is insurmountable. Discovering a path forward requires more than data center consulting and project management — it requires a strategic understanding of mission-critical applications and systems, paired with an ability to coordinate software vendors and consultants that can seamlessly migrate from aging and version-locked software to more modern, open operating systems and applications.
On the public safety side — where there has always been a need to collaborate and analyze data — agencies seek to take their information technology to the next level. As more public services are performed digitally or have a digital component, agencies have seen an exponential increase in the need for server storage and data center capabilities. Most governments are required to store information for many years — much longer than the private sector — to protect that data from unauthorized use, abuse or theft. As such, data centers are asked to fulfill missions that would seem unimaginable just five or 10 years ago.
Accommodating the information needs of today's agencies and constituents, with a strong vision for how technology will advance in the next three to five years, is critical to supporting evolving missions for state and local government demand management.
Managing risk
Both growth and cost challenges to today's government data centers work within a much larger and more sinister context as well: data theft and loss. With the internet, the Internet of Things (IoT) and the flood of public data being digitized, the big data explosion requires more storage and larger infrastructure, accommodating bigger files and more powerful networks to transport them — all of which incrementally increase security risks.
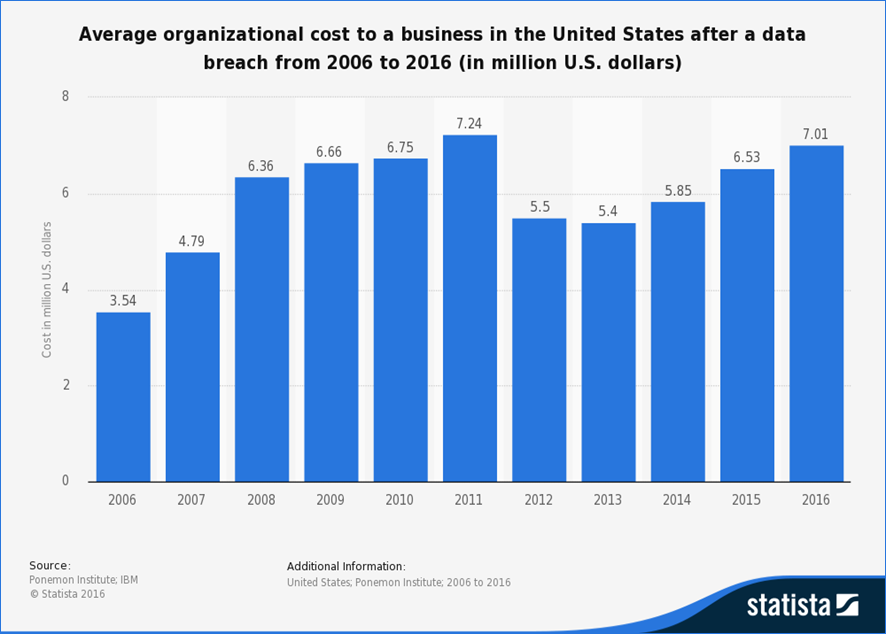
High-profile data breaches are increasingly common, costing billions in damages and distractions, putting IT infrastructure under intense (often political) scrutiny. In 2016, the average cost to businesses affected by recent data breaches in the United States amounted to $7.01 million — as shown in Figure 2.
With the number of break-ins and the damages caused by data breaches on the rise, data centers are forced to perform a high-risk balancing act — driving more data, accessibility and capability without increasing their agencies' or constituents' vulnerability in the process.
Furthermore, emerging mobile and cloud computing models expose state and local governments to new security risks compounded by the social networking and collaborative nature of today's constituents and government workforce. IT managers delivering new mobile and cloud solutions must plan to mitigate the increased risks of data theft, fraud and privacy breaches. Unfortunately, such security plans negatively impact agility, maintenance burdens and IT costs, adding another layer to the existing challenges of data center management.
Even supply chain security is a hot topic with government agencies often asking data center vendors, “How do you secure your supply chain management?” Agencies need to ensure the security of network devices from manufacture through installation and deployment, combating instances where something embedded into the device’s hardware or firmware may present a security compromise. Data center discovery therefore needs to include a supply chain element, defining provenance and tracking the logistical path of system hardware, software, appliances and applications along their entire lifecycle.
Once again, an understanding of the missions served by the data center also requires a holistic and comprehensive security mentality that spans far beyond the walls of the data center or even the firewalls of the network. Risk management must peer back to the creation of data center solutions, as well as forward into its deployment for a mobile workforce and constituency.






