Achieving stronger cybersecurity outcomes
Sophos provides advanced security solutions, available from Insight, tailored for various industries, cloud environments, specific use cases, and compliance requirements.

Strengthen your ransomware defenses.
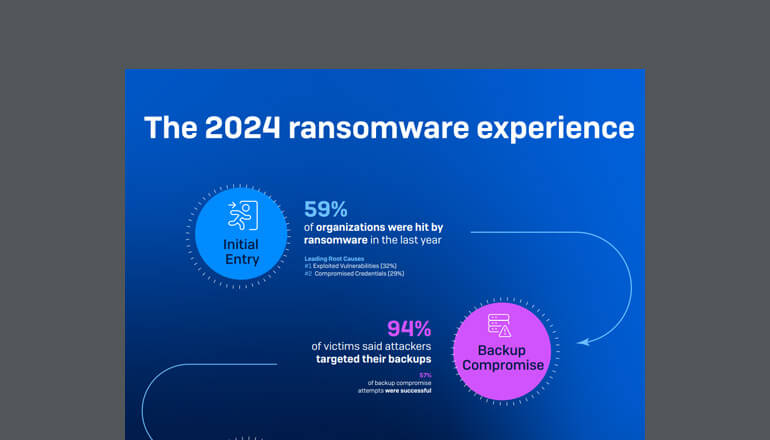
In the past year, a significant number of organizations experienced ransomware attacks, making it the leading cause of cyber insurance claims. To effectively combat ransomware, it's essential to implement robust and flexible defense technologies throughout your environment, complemented by 24/7 human-led detection and response via XDR or MDR. Enhance your security further with Sophos Email, Sophos Firewall, and Sophos NDR.
Extend protection to all of your endpoints.
Your network is constantly evolving as information travels between locations. With Sophos, you can secure every laptop, virtual desktop and server — along with mobile devices.
Sophos Intercept X
Using Cryptoguard, Intercept X with EDR ensures your data is protected from encryption by ransomware — keeping your files and data safe.
Sophos Endpoint Protection
With next-gen security, Endpoint Protection includes simple, speedy deployment and unmasks malware while synchronizing your security.

Managed Detection and Response
Our highly skilled experts monitor, investigate, and respond to threats 24/7 — executing immediate, human-led response actions to stop attacks.
Sophos Mobile Control
Keep your users productive while securing all mobile devices accessing your network, and manage it all through Sophos Central.

Optimize cyber insurance
Insurers widely recognize that using a managed detection and response service such as Sophos MDR is one of the best ways to reduce cyber risk. Read the whitepaper to discover how you can achieve multiple cyber controls required for cyber insurance.