Article Microsoft Enterprise Mobility + Security: Mobile Device and Application Management
The industry is buzzing with terms like Bring Your Own Device (BYOD), Bring Your Own Technology (BYOT) and Choose Your Own Device (CYOD).
By Isabel Ticlo / 27 Feb 2017 / Topics: Mobility , Modern workplace , Cybersecurity

Devices are now an alarm clock, health tracker, web browser, email client and music player. And they’re distracting, especially at the office. So how can we minimize the interruptions from our phones to increase productivity at work? Here are a few tips:
- Turn off notifications — That newsflash or social post is probably completely unrelated to your work. If you’re an iPhone user, you can also use the built-in Do Not Disturb feature to control who, if anyone, can reach you during the day.
- Delete your biggest time-sinks — Remove the apps that make you lose time. If you can’t bear to do that, move them off your home screen or hide them in folders so they aren’t staring at you any time you do need to use your phone. Like they say —out of sight, out of mind.
- Use a No Second Screen policy for meetings — Don’t just silence your phone, but also turn it screen-side down during meetings, whether online or in person, to help you remain focused on the task at hand.
Area 3: Effectively manage inbox emails.
It’s possible that you’re just now feeling caught up with the email you received over the holidays. Or maybe you’ll never really feel that way — the struggle is real. Having an email organization strategy and a few email management tips can be a lifesaver when you’re getting back to the office after a few well-deserved days off:
- Select times — Save your highest-energy times for getting your bigger projects done. If you’re just not a morning person, go through your inbox for the first 30 minutes to get settled into work mode. An email reply schedule such as early morning, just before lunch and before you leave for the day may work well for you.
- Use rules — Most email programs will categorize your emails into separate folders automatically using rules. Creating too many may be a detriment, but a few broad categories can help filter out the newsletters and non-critical email we’re all subject to.
- Quality over quantity — Take extra time to clearly articulate the answer to a question or to ask for more information. Being accurate in your writing should prevent additional clarification emails.
- Respond to the newest first — It may be tempting to start with the emails that have waited the longest for a response, but if you’ve been out for a week, chances are those requests were already handled.
- To maintain your current inbox status, you may be interested in the “Yesterbox” method endorsed by Zappos’ Tony Hsieh, in which the premise is to focus on anything that came in yesterday, leaving everything from today or from before yesterday to another time.
Mobility isn’t slowing down, and personal laptops, tablets and smartphones are quickly taking over the workplace. With the need increasing for employee mobility, businesses are exploring solutions that provide a more flexible, efficient, and collaborative user experience that empowers employees to work anytime, from any device, anywhere. In fact, it’s now almost expected that businesses enable employees to work anytime and anywhere.
What does this mean for mobile device and application management? Let’s find out.
Going mobile? No problem.
In this day and age we use our mobile devices for a number of reasons ranging from signing into email and banking applications, to browsing the web and social media. We utilize these third-party applications — and give them permission to grant access to other third-party sites when needed — to keep our lives in order and to share our lives with our friends and family. What we don’t think twice about, is that businesses can also see our activity and use this information to target us with personalized ads. While this might be acceptable on a personal level, what happens when we bring our own device into a professional work environment? Our personal devices suddenly become gateways to critical company information.
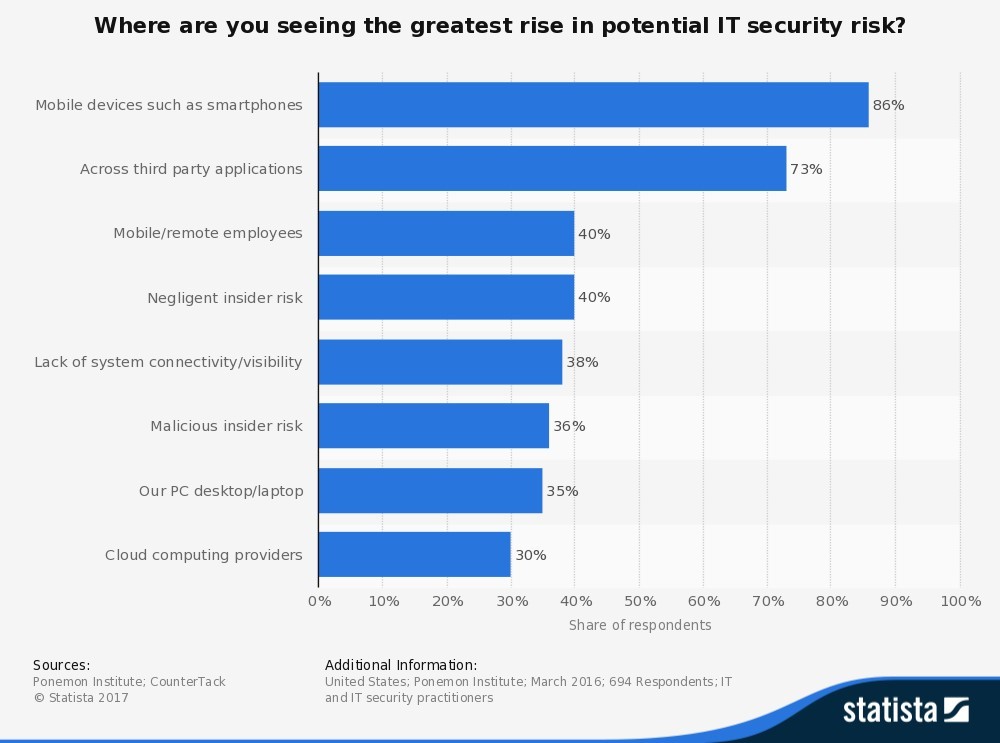
Figure 1 depicts the results from a survey that the Ponemon Institute conducted in 2016, asking 694 IT professionals in the United States, “Where are you seeing the greatest rise in potential IT security risk?” 86% declared that mobile devices, such as smartphones, were the biggest threat to endpoint security. Subsequently, 73% said across third party applications and 40% said mobile/remote employees. While we have grown accustomed to the many noticeable benefits of the BYOD movement — such as greater job satisfaction and flexibility — it’s still necessary to take steps to ensure that client information, employee credentials and organizational data are secure.
Enterprise Mobility + Security has you covered.
Microsoft Enterprise Mobility + Security (EMS) provides flexible, comprehensive solutions that help businesses empower employees to access all of their data and applications from every device and every location. With EMS, you get complete access to services that will help you:
Control identity and access in the cloud.
- Get identity-driven security.
- Protect your corporate data.
- Enable secured collaboration.
- Manage mobile devices and applications.
With EMS, you not only protect data that is vital to the success of your organization, but also identify where security breaches might occur before they damage your finances or reputation.
Device security is a must.
Let’s take a moment to focus on mobile device and applications management. Microsoft Mobile Application Management (MAM) and Mobile Device Management (MDM) solutions are designed to help businesses easily deliver administrative capabilities either on premises, in the cloud or through a hybrid platform — all from one console.
When you choose EMS, you are choosing a more secure and seamless transition to a primarily mobile-driven environment. With the EMS E3 bundle, you also gain access to best-in-class Microsoft solutions to better protect data.
Windows Intune: Your employees want their personal devices to seamlessly integrate with their work requests. The faster they are able to log in to the company’s system, the sooner they can start assisting clients. That means you need an operating system that will ensure user devices remain compliant while enabling IT to securely register and manage applications across multiple sectors. Windows Intune is your hassle-free guide to greater workforce security and enablement.
Azure Active Directory Premium (AADP): Remembering a handful of passwords can be challenging and frustrating. With AADP, you get a single identity and password for all approved internal and third-party applications. Plus, self-service password resets reduce the cost of IT support. What if a suspicious individual figures out the login information of one of your teammates? AADP advanced reporting alerts will make sure you’re notified that an unconventional IP address or device is trying to infiltrate the system.
Azure Information Protection Premium (AIPP): Prioritizing endpoint security is a must — this includes phones, tablets, laptops and printers. But what happens if a hacker somehow manages to slip through your defenses? It’s important to be extra cautious and make sure that those who sneak in can’t do anything with your data once they’ve accessed it. That’s why AIPP allows users to specify who can open, modify, print or forward content.
Advanced Threat Analytics (ATA): While it’s important to have a backup plan like AIPP, it’s equally important to have a preventive plan in place to identify advanced persistent threats before they occur. ATA uses behavioral analytics to provide an actionable report to help your business quickly take action.